Introduction — The PII Challenge in Modern BI
Define the Stake: PII and Why it Matters —
PII (Personally Identifiable Information) includes data like emails, names, and SSNs. Handling it securely is non-negotiable due to three critical factors:
- Legal Compliance: Strict regulations (GDPR/CCPA) impose massive fines for non-compliance.
- Brand Trust: Data breaches instantly erode consumer confidence and reputation.
- Financial Impact: Costs include fines, investigations, and managing customer fallout.
Protecting PII is essential to avoid severe penalties and maintain consumer trust.
The BI Dilemma: Value vs. Restriction
The core conflict in modern BI is balancing data utility with the mandate for data privacy.
- Analyst’s Need (Value): Analysts require detailed, granular PII (like user IDs) to accurately calculate high-value metrics (e.g., customer lifetime value, churn rate).
- Compliance Mandate (Restriction): The same granular data must be restricted, masked, or anonymized to eliminate legal and reputational risk (GDPR/CCPA).
The dilemma is delivering actionable insights without exposing the underlying sensitive data.
Looker’s Advantage (The Hook)
Looker’s advantage is its LookML layer, which resolves the PII dilemma by shifting security enforcement from the fragile front-end to the semantic modeling layer.
Traditional BI tools apply security after querying the raw data. Looker embeds security rules directly into the data model itself, ensuring:
- Security is Built-in: PII masking and filtering rules are coded directly into LookML.
- Enforcement is Universal: Every query (UI, dashboard, API) must pass the LookML security checkpoint first.
- Auditability: Rules are centralized in version-controlled code, creating a single, verifiable source of truth for all data governance policies.
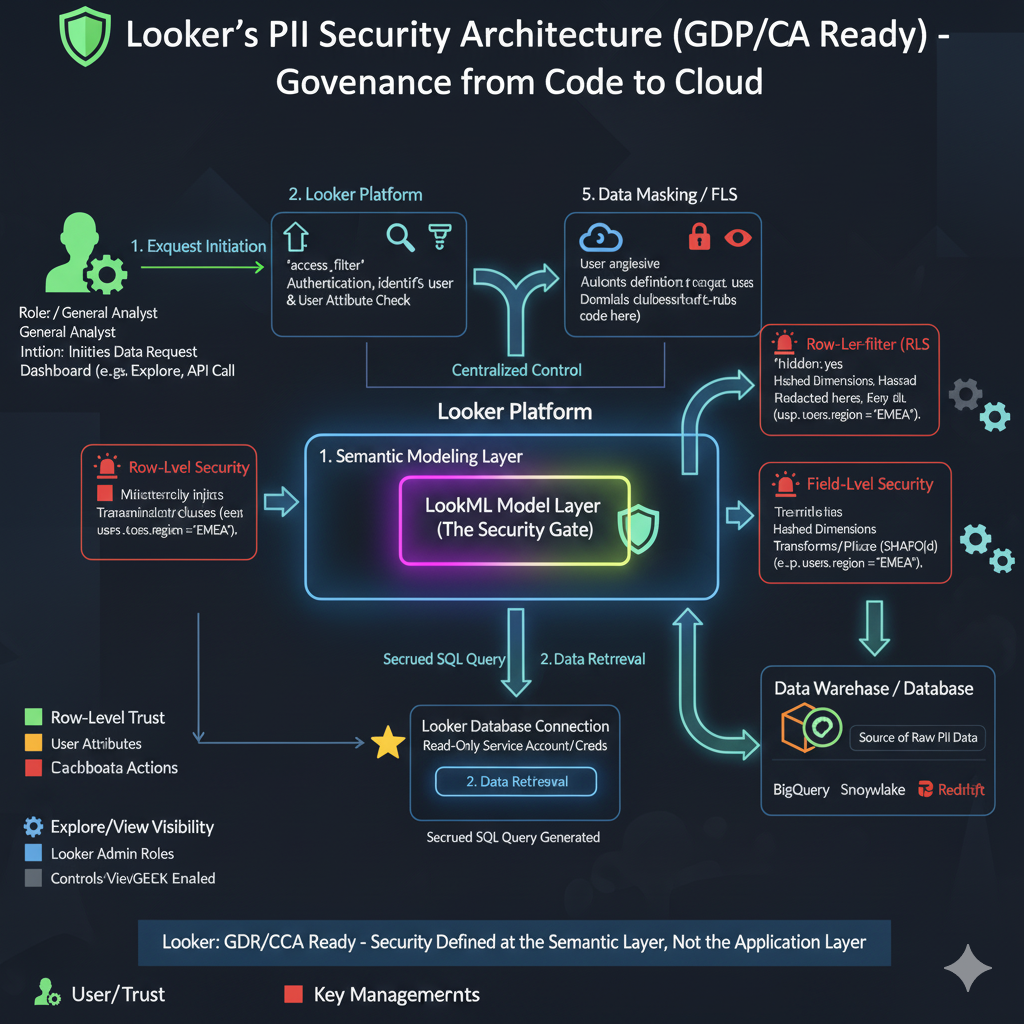
LookML: The Zero-Trust Data Model
LookML provides four primary mechanisms to ensure that security is defined and enforced at the semantic modeling layer, preventing unauthorized exposure of PII (Personally Identifiable Information).
User / Data Consumer :
The journey begins with any user interacting with Looker. Whether they are a “General Analyst” exploring data, a “PII Viewer” compliance officer, or an automated system via the Looker API, their identity is authenticated. Looker then identifies their assigned Roles and User Attributes (e.g., user_country: 'US', pii_admin: true), which dictate their access rights.
Looker Platform — The Gateway
This is the initial entry point where Looker receives the user’s data request. It acts as the central orchestrator, managing user sessions and preparing the request for the core security layer.
LookML Model Layer — The Security Brain :
This is the heart of Looker’s PII security. All data definitions, relationships, and crucially, all PII protection rules are hard-coded into LookML. Every single data query, irrespective of its origin, must pass through this layer. It acts as the “semantic layer,” translating business questions into secure SQL and enforcing governance policies universally.
1. Row-Level Security (RLS) — access_filter :
Based on the user’s User Attributes, LookML dynamically injects a WHERE clause into the SQL query (e.g., WHERE users.region = 'EMEA'). This ensures users can only see the specific rows (records) of data they are authorized for.
2. Field-Level Security (FLS) — Masking & Hiding :
LookML transforms or conceals sensitive columns (fields). This includes:
hidden: yes: Making raw PII fields (like Social Security Numbers) completely invisible in the UI.- Hashed Dimensions: Creating irreversible, unique identifiers (e.g.,
SHA256(${users.email})) for analysis without exposing raw emails. - Redaction/Obfuscation: Partially masking data (e.g., showing
***-**-1234for a phone number).
3. Explore/View Visibility :
Beyond filtering data, Looker’s Admin settings with Roles and Permission Sets control whether entire Explores or specific Views (and their fields) are even visible to a user. This is a higher-level gatekeeping mechanism for sensitive data sets.
Looker Database Connection
This highlights that if your data warehouse (e.g., BigQuery) is encrypted with CMEK, the service account Looker uses to connect must also have specific IAM permissions to use your KMS key. This ensures that even Looker, though authorized by its own roles, still needs your key to decrypt the data it reads. This provides a critical layer of customer control over key management.
Data Warehouse / Database :
- This explicitly states that the raw PII data residing in your database is encrypted when it’s stored.
- GMEK (Google-Managed Encryption Keys) is the default, where Google handles key management.
- CMEK (Customer-Managed Encryption Keys) offers you greater control, allowing you to manage the encryption keys via Google Cloud KMS, adding another layer of security and compliance for data at rest.
Result Presentation ( Filtered & Masked):
The database returns the query results to Looker, which then presents only the authorized, filtered, and/or masked data to the user in their dashboard, Explore, or API response. User Roles and Permissions also govern capabilities like data download, ensuring only authorized individuals can export even the already secured data.
Governance, Auditing, and Architecture
This section outlines the essential organizational and technical controls needed outside of the LookML code itself to maintain a compliant and secure environment when dealing with PII. It focuses on the governance framework that surrounds Looker.
Role & Permission Segmentation
Effective PII protection requires a highly restrictive security model based on the Principle of Least Privilege.
- Need for Segmentation: You must define granular Roles and Permission Sets to segregate users based on their job function and access needs, preventing unauthorized access to sensitive data.
- Example: A “PII Viewer” role is granted permissions to see masked PII, while a “General Analyst” role is completely restricted to aggregated data only.
- Controlling Capabilities: Permissions must also govern system actions like Data Download. Only highly trusted roles should be allowed to export query results containing unmasked PII.
The Audit Trail (System Activity)
Compliance regulations (like GDPR and HIPAA) demand proof of who accessed PII and when. Looker’s built-in auditing tools fulfill this requirement.
- Looker System Activity: These are specialized, internal Looker models and Explores that track all user and system actions. They provide a comprehensive audit trail.
- What it Audits: You can use these models to query the history of actions, specifically:– Who ran the query (user ID), What the query was (the generated SQL),When it was executed and how long it took.
- Crucial for Compliance: This provides the necessary evidence to demonstrate data governance and investigate any potential policy violations.
Secure Architecture (Contextualizing Looker)
Looker acts as the security enforcement layer, but the entire data ecosystem must be secured.
- Wider Data Stack Security: Looker is only as secure as your underlying database/data warehouse (e.g., BigQuery, Snowflake). Direct, unrestricted access to the source data bypasses all LookML rules.
- Read-Only Connections: Always configure Looker’s database connection credentials with read-only access. This crucial step prevents Looker from being used to accidentally or maliciously modify, delete, or inject data into your source systems.
This architecture ensures the LookML Model enforces PII rules before the request ever reaches the Data Warehouse.
Conclusion — Building Trust with Data
The journey through the enhanced security flow demonstrates a single, powerful truth: PII protection should never be an afterthought; it must be embedded in the architecture.
By centralizing all security rules within the LookML Model Layer, organizations move past fragile, front-end security controls. This approach ensures that every single query — whether from a dashboard, an API call, or an Explore — is automatically subjected to Row-Level Security (RLS) and Field-Level Security (FLS) before the database is ever touched.
This robust, auditable framework not only satisfies the stringent demands of GDPR and CCPA but fundamentally transforms Looker from a visualization tool into a true Data Governance Platform. Ultimately, adopting this LookML-first strategy is the clearest way to build and maintain the necessary trust with your customers and regulators.
Source Credit: https://medium.com/google-cloud/beyond-dashboards-how-to-implement-robust-pii-security-in-looker-gdpr-ccpa-ready-5e48b44cd70f?source=rss—-e52cf94d98af—4




