Gemini Code Assist agents Gemini Code Assist for GitHub, released on February 25 in a public preview...
GCP
And using code2prompt, yet another CLI tool for this purpose, yields a token count of 57,160,552. What’s...
As organizations adopt DevOps practices, application developers are increasingly expected to not only build applications but also...
Ever felt like setting up your cloud networking infrastructure was a bit like trying to untangle a...
The world of generative AI is moving fast, with models like Lyria, Imagen, and Veo now capable...
Welcome back to this Multimodal Live API article series. 📚 To explore previous articles in this series,...
Build AI-powered applications Aiven for AlloyDB Omni integrates seamlessly with Aiven’s unified data platform, providing the tools...
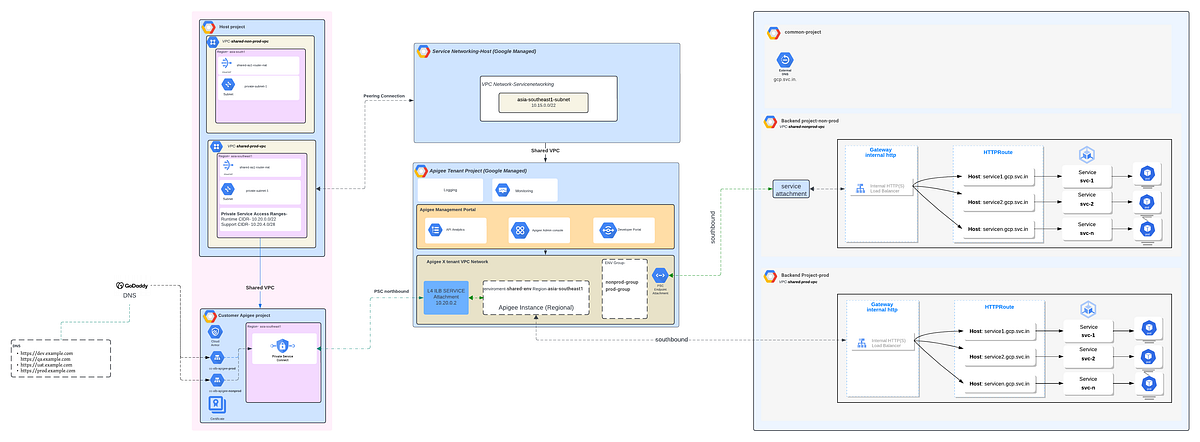
Networking Considerations We have two VPC’s one is Prod (prod-vpc) and another for non-prod (non-prod vpc).The Apigee...
The liquid cooling imperative The dramatic increase in chip power consumption — from 100W chips to accelerators...
The world of genomics is undergoing a seismic shift, and Artificial Intelligence is the driving force. We’re...